Vulnerability Management
Vulnerability management in the manufacturing industry is the continuous process of identifying, assessing, prioritising, and remediating security weaknesses across industrial systems to protect production operations and maintain resilience against cyber threats.
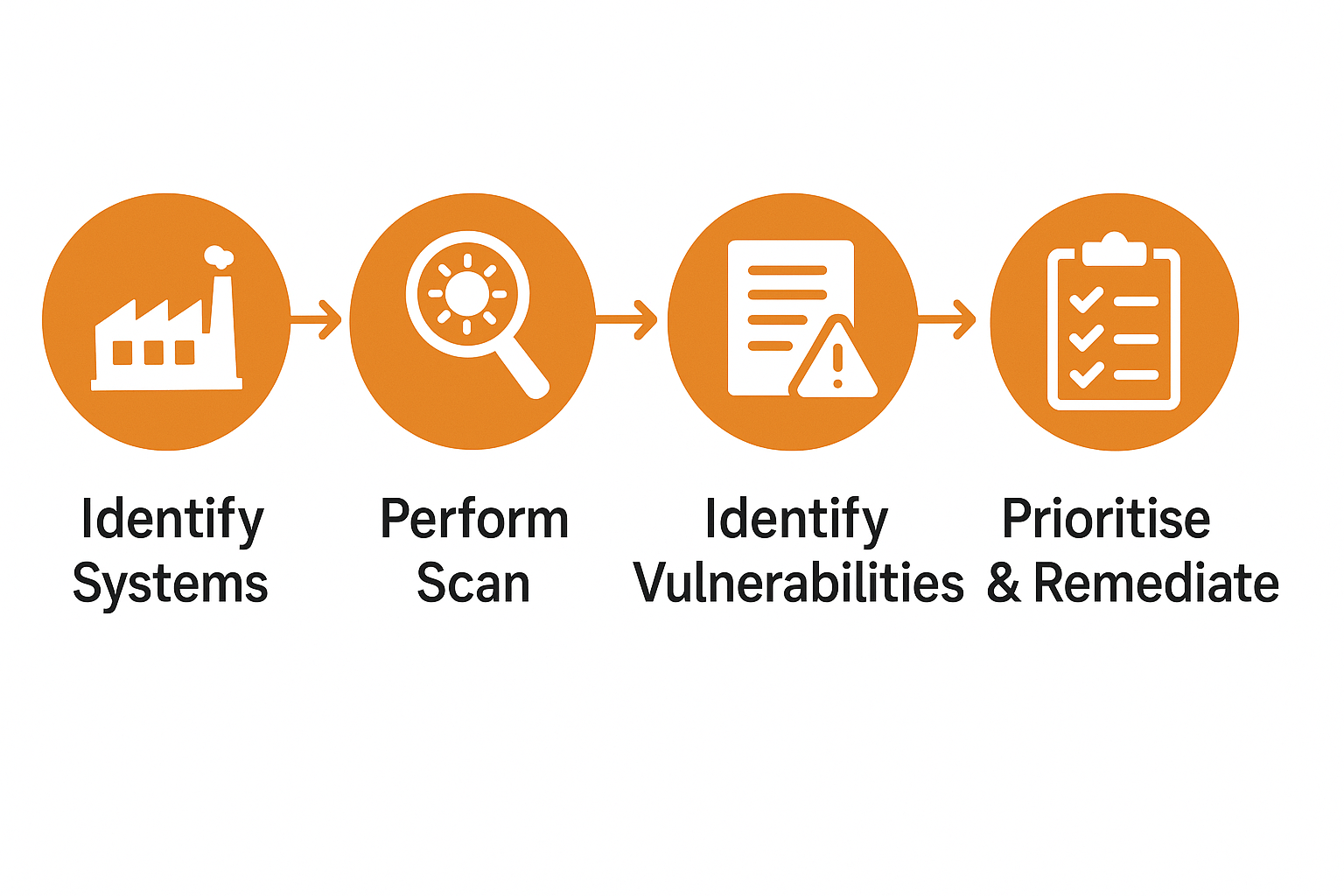
Vulnerability Management Process in the Manufacturing Industry
-
Manufacturing environments use interconnected systems and operational technology that are vulnerable to cyberattacks
-
Identifying systems helps organisations understand all assets, including older equipment lacking built-in security
-
Prioritising and remediating focuses efforts on the most critical risks that could halt production, compromise safety, or expose data
-
Failing to follow these steps leaves organisations exposed to cyber incidents that can disrupt production and undermine business continuity
Enhance and Evolve Your Security Posture
As vulnerabilities and threats continue to emerge daily, now is the time to strengthen your security posture. Your organisation needs a robust vulnerability management programme that actively scans your environment for harmful vulnerabilities and prioritises them based on critical security criteria.
Anzen Secure's Vulnerability Management grants complete visibility of all vulnerabilities across your organisation's network. These vulnerabilities are mapped to known threats and prioritised for swift remediation, enabling you to quickly identify those most likely to attract attackers and resolve them before they can be exploited.
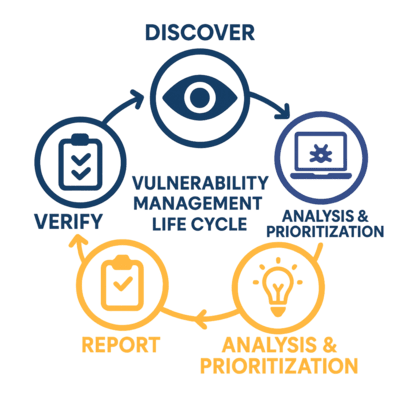
Vulnerability Scanning
Anzen Secure offers end-to-end vulnerability management service designed to transform data into clear insights about your networks security weaknesses and identify hidden vulnerabilities.
Key Features
-
Advanced Vulnerability Scanning with cutting-edge scanning processes
-
Cross-Sector Intelligence leveraging insights from diverse sectors
-
Detailed Analysis to pinpoint areas of concern
Benefits
-
Enhanced Security Posture with clear understanding of network vulnerabilities
-
Rapid Remediation through swift action on identified vulnerabilities
-
Peace of Mind